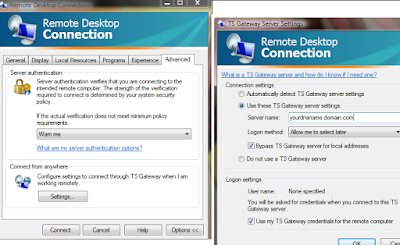
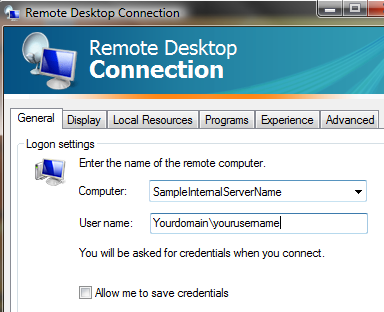
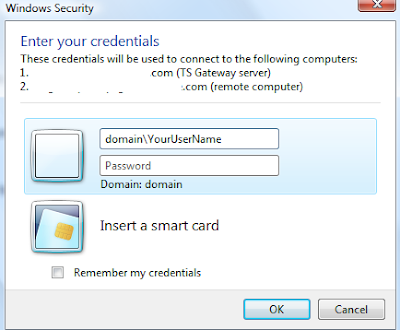
Okay, I know I can be a bit slow on the uptake for some of these powershell commands but this one took way too long to get right. All the nice friendly examples from msdn leave out the Identity parameter. Powershell will be more than happy to barf an error back to you if you leave it out.
http://technet.microsoft.com/en-us/library/bb124149.aspx
Just what is this identity thing anyway? It's pretty much your CAS_Servername\rpc (Default Web Site)
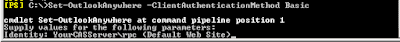
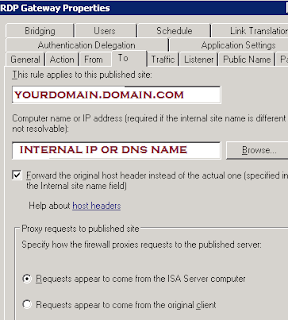
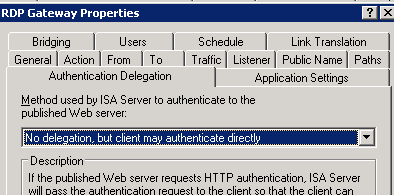
So next you're asking why am I bothering since we've got a nice GUI, etc for setting up outlook anywhere and the permissions on the IIS folder /rpc. Well, through the careful string of failures at getting NTLM to work transparently through my ISA server (whilst still requiring rpc validation at the isa server itself), I determined that Basic authentication was good enough for me. But I still use NTLM for the web publishing rule from the ISA server to the exchange CAS server. With the advent of SP1 for exchange 2007, you can easily setup your server to use different combinations of Basic and NTLM for the Outlook Anywhere and RPC folders respectively. When your server generates AutoDiscover.xml it provides the client with the authentication level that is specified in the -ClientAuthentication Method. But if you want your ISA server to communicate with the exchange CAS with NTLM, then you have to set the -IISAuthentication parameter. (yeah, headaches abound). To see what your CAS server is using, run Get-OutlookAnywhere from powershell
ClientAuthenticationMethod : Basic
IISAuthenticationMethods : {Ntlm}
In summary:
1. My remote users have outlook 2007 sp1 and get autoconfigured to use Basic Auth.
2. My ISA server publishing rule uses NTLM for Authentication Delegation.
3. My rpc folder in IIS just has Integrated Auth checked.
For more information including how to setup an Exch 2007/ISA 2007/Outlook Anywhere/etc check out the following links:
Great tutorial by Thomas Shinder - covers everything from the setup of the exchange server, through the publishing in ISA all the way to the outlook client config:
http://www.isaserver.org/tutorials/Publishing-Exchange-2007-OWA-Exchange-ActiveSync-RPCHTTP-using-2006-ISA-Firewall-Part1.html
The ever reliable petri database:
http://www.petri.co.il/outlook_anywhere_2007_w_isa_server.htm
More info on the set-outlookanywhere syntax:
http://www.exchange-genie.com/2008/02/configuring-outlook-anywhere-for-exchange-2007-sp1/
Paper on setting up transparent authentication/NTLM with isa 2006 and exchange 2007. I did eventually get it to work in a test environment.
http://blog.msfirewall.org.uk/2008/07/publishing-exchange-2007-services-with.html